NSSRound#1 Basic
2022-08-03 23:37:08
# WEB
# basic_check
发现允许 PUT 方法请求
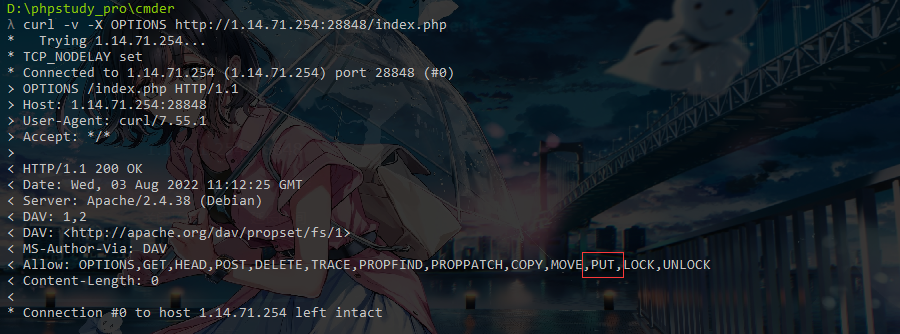
1 | PUT /shell.php HTTP/1.1 |
写入一句话
rce 即可
# Basic]sql_by_sql
先注册,进去有个修改密码
可能是二次注入
修改密码处源码
1 | <!-- update user set password='%s' where username='%s'; --> |
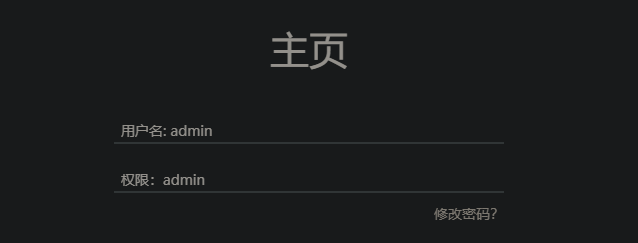
重新注册一个 admin--+
获得 admin 身份
在 /query 下查询
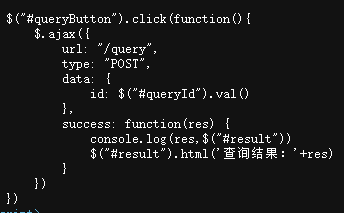
1 | #!/usr/bin/python3 |
# MISC
# cut_into_thirds
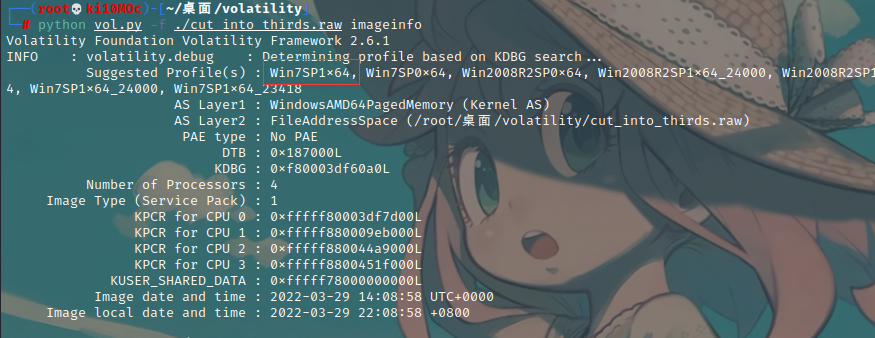
1 | python vol.py -f ./cut_into_thirds.raw imageinfo |
得到版本号
1 | python vol.py -f ./cut_into_thirds.raw --profile=Win7SP1x64 pslist |
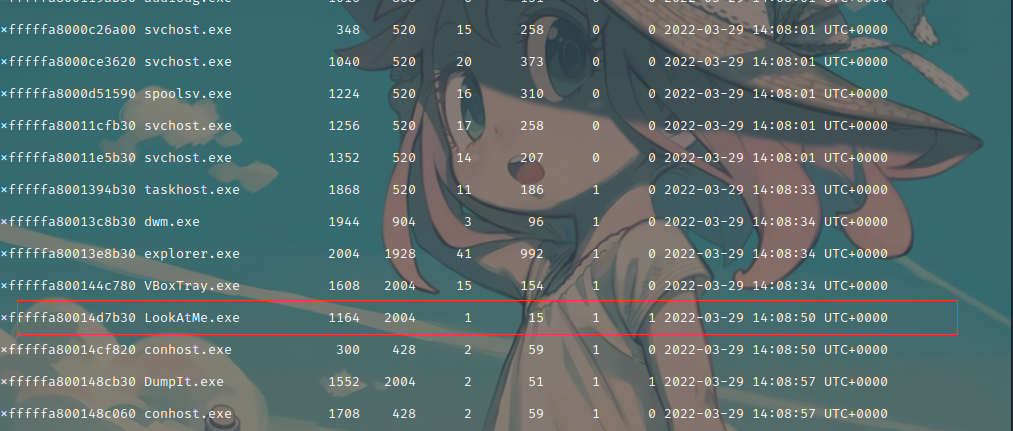
这有个引人注意的进程
获取 dump 文件
1 | python vol.py -f ./cut_into_thirds.raw --profile=Win7SP1x64 memdump -p 1164 -D ./ |
foremost 分离得到 part1
1 | part1:3930653363343839PK? |
直接 dump 目标文件
1 | python vol.py -f ./cut_into_thirds.raw --profile=Win7SP1x64 procdump -p 1164 -D ./ |
并查找相关信息
1 | strings ./executable.1164.exe |
得到 part2
1 | part2:GRRGGYJNGQ4GKMBNMJRTONI= |
最后查看用户信息得到 part3
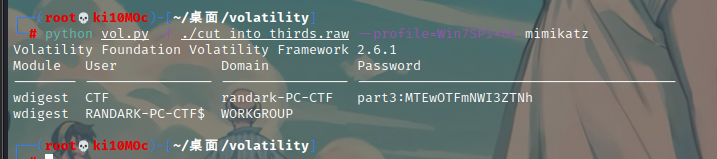
分别进行 base16、32、64 解密即可
